When I saw the Discord Forensics challenge on LetsDefend, it reminded me of some recent data leak incidents involving members of the US Air Force using the popular gaming community’s instant messaging and VoIP social platform Discord. And, so, I wanted to try how to investigate Discord artifacts. Below are some of the headlines showing the incidents: 

LetsDefend rated this challenge as Medium difficulty, but I feel it should have been under easy level. This Blue Team challenge can be accessed at https://app.letsdefend.io/challenge/discord-forensics. I used a Windows machine and the tools Thunderbird (email application), ChromeCacheView, Chrome Browser, and PowerShell.
Scenario: Our SIEM alerted that AV blocked malware from running on an employee’s machine. For further investigation, the incident response team quickly acquired an image of the machine. To find out how this malware got on the machine, the task is to find the entry point of the attack and trace the attacker.
- What is the name of the attacker?
- a*********
- This challenge is discord forensics, but the attacker used another method for the initial correspondence. Looking through the disk image acquired for investigation, it seems like the other form of communication besides Discord is email:

- Open the email messages using any email client and look for the attacker’s name. I am using Thunderbird.

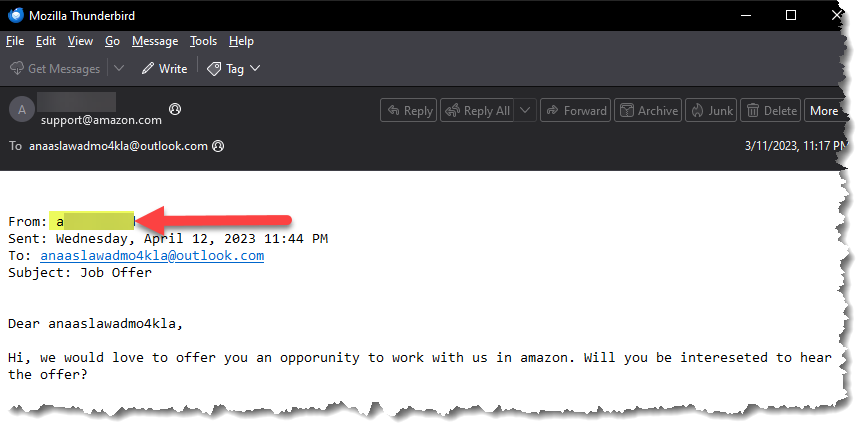
- What application is used for messaging?
- D******
- The title of this challenge should give away the answer to this question.
- What is the attacker’s username on the application?
- a*******
- If you follow the steps we took in question number 1, you should see the attacker’s username in one of the emails.

- When did the attacker send the first message to the victim on this application?
- 2***-**-**T**:**:**
- First, we have to locate where Discord artifacts are stored: C:\Users\%user%\AppData\Roaming\discord\cache
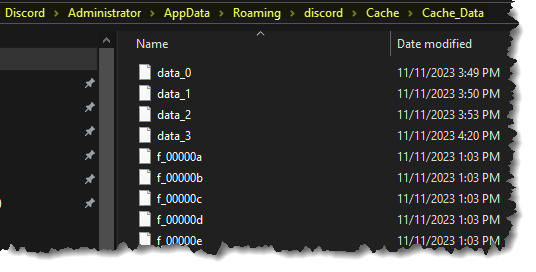
- Second, we are going to view the data using the tool ChromeCacheView. Load the cache_data folder:

- Once the data are loaded into ChromeCacheView, sort the information using Filename. Scroll down until you see the filename 50.json. And if you look at the URL column, these are the only files with the word “messages” in their query:

- Since these are json files, you can open them using a text editor, but I found using any browser easier. Open all 5 files using any browser by right-clicking on each of the files and choosing Open Selected Cache File With and choose any browser (I used Chrome).

- Now, search for the attacker’s username and check the timestamp:
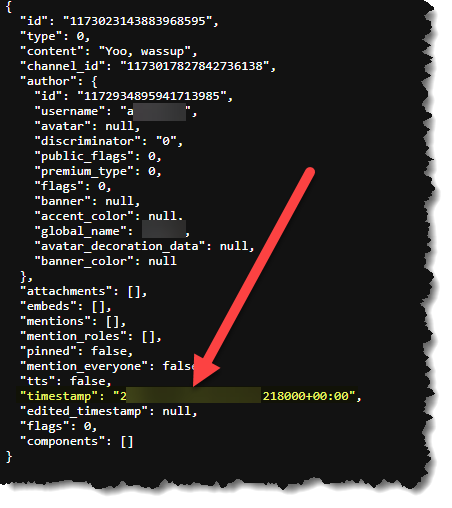
- The attacker has sent a server invitation URL to the victim, what is the full URL?
- https://*******.**/*********
- Since we are looking for a URL, it would make sense to do ctrl+f and search for https

- How many people were on the Discord server?
- *
- Do the same steps as in question number 5, but this time, search for a username and keep track of the number of unique username entries.

- What is the MD5 hash of the attachment file that the victim sent to the attacker?
- 4*******************************
- The steps are the same as above, but since we are looking for an attachment, let’s search using the word filename.
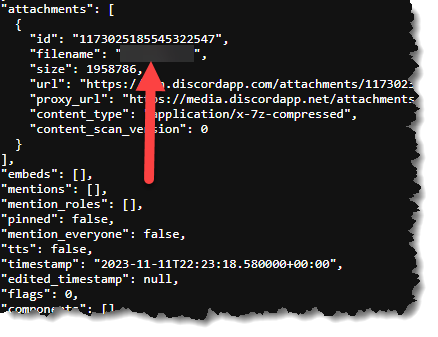
- Now that we know the file’s name, let’s look at the common locations where files are stored, such as the Desktop, Downloads, Documents, etc.
- We located the file in the Documents folder. Retrieve the hash using Powershell. Type get-filehash -algorithm MD5 Type_Filename_Here

- What is the victim’s country?
- F*****
- Look at the Filename column in your ChromeCacheView tool, and you will see country_code

- What is the URL of the attachment that the attacker sent to the victim?
- https://*****.******.**/********.***
- For this question, we have to go back and look at the email chain again.
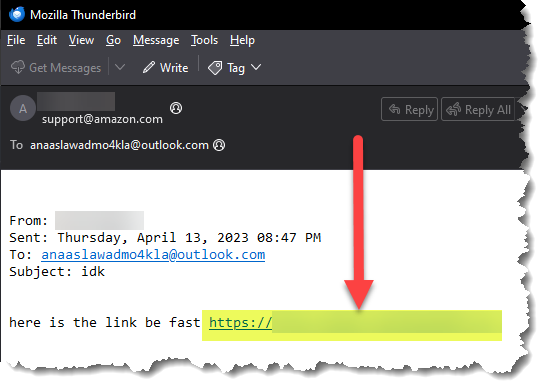
And that’s a wrap. I am guessing this is how they acquired incriminating evidence against the Airmen who leaked data through Discord.
Hope we all learned something new. Please subscribe to my blog. Salamat po!
Yeah good one. Hits “close to home”.
LikeLike