This room was released on 11/11/2021 and it is rated hard in difficulty. Shout-out to the room creators, @RussianPanda [She/Her] and @heavenraiza. You can access the room at https://tryhackme.com/room/squidgameroom.
This is room is more on the blue side of the cybersecurity field. The skills/tools to be tested and needed to eliminate the five attackers in this room are Oletools, Oledump, OfficeMalwareScanner, CyberChef, and hybrid-analysis.com which is an online free malware analysis service that detects and analyzes unknown threats.
What you will find in this blog is my way of utilizing different tools to analyze malicious documents. You will notice how I jump on to different tools because there is not one single tool to rule them all. In the real world, you are not limited to a specific tool to do analysis, you can use whatever tool you are comfortable with using as long as you get your answers. I intentionally masked parts of the answers so you will have to do the steps to find the entirety of the answers.
Attacker 1:
- What is the malicious C2 domain you found in the maldoc where an executable download was attempted?
- f************.****/***_****-***/****.***?*=*******.**s
- I uploaded the attacker.doc to hybrid-analysis.com, and found the encoded process below:

2. Copy the highlighted string and decode it using Cyberchef, and use from Base 64, Remove whitespace, and Remove null bytes as shown below to get the C2 domain name:

- What executable file is the maldoc trying to drop?
- Q****.**e
The executable file can also be found from the decoded process we attained previously:

- In what folder is it dropping the malicious executable?
- %P**********%
I just guessed the answer above without looking for it as it uses a very common folder.
- Provide the name of the COM object the maldoc is trying to access
- S****************w
From the decoded powershell script that we did previously, we can see that there is an entry for a $clsid=New-ObjectGuid ‘C08AFD90-F2A1-11D1-8455-00A0C91F3880’ and if we search for that string on Google:

- Include the malicious IP and the php extention found in the maldoc
- 1**.**.**.**/****.**p
This information can also be found in the decoded powershell script:

- Find the phone number in the maldoc
- 2**-***-***7
- We can run the strings command from the terminal. Enter strings attacker1.doc:

2. Scroll up close to the beginning of the results from running the strings command and you will see the phone number:

- Provide the time when this document was last saved
- 2***-**-** **:**:*0
For this information, you can use the tool oletimes to pull both the document’s creation time and modification time. Run oletimes attacker1.doc
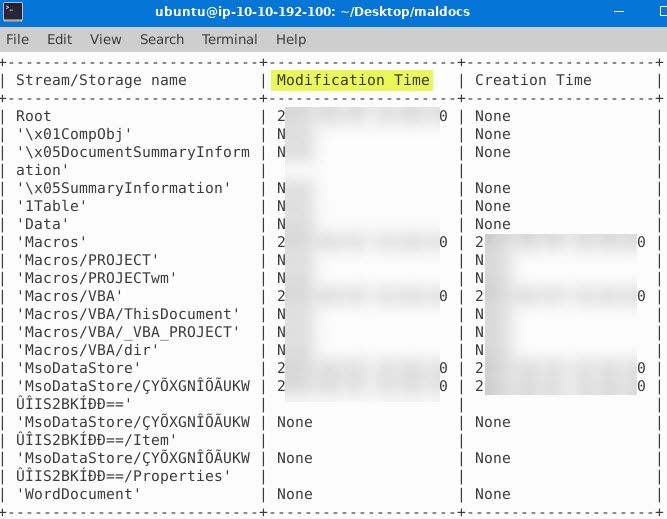
- Provide the stream number that contains a macro
- *
This time we are going to use the tool oledump.py. When you see the result, look for the stream with the uppercase M on it. The uppercase M signifies that a non-standard macro is present in that stream. Run oledump.py attacker1.doc:

- Provide the name of the stream that contains a macro
- T**********t
Look at the image just above this question to get a visual.
Attacker 2:
- Provide the streams that contain macros
- 1*, **, **, *6
We are going to use oledump.py tool again. Again, just look for the uppercase M as the marker for the streams with macros. Run oledump.py attacker2.doc
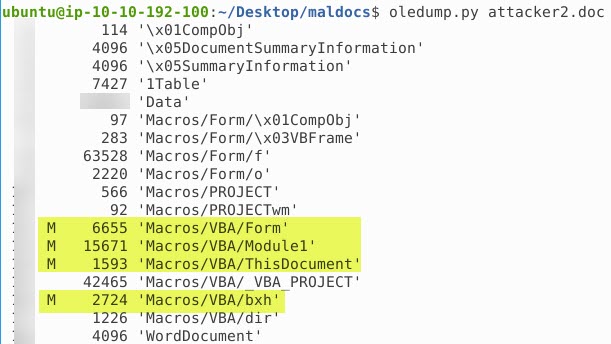
- Provide the size of the compiled code for the second stream that constains a macro
- 1***7
If you look at the image above this question the second stream is the Module1. You can see the total size of Module1, but the question is asking the size of the compiled code for the second stream, meaning a smaller number than what you can see above. We are going to add the option -i in oledump.py to get more information. Run oledump.py attacker2.doc -i

- Provide the largest number of bytes found while analyzing the streams
- 6***1
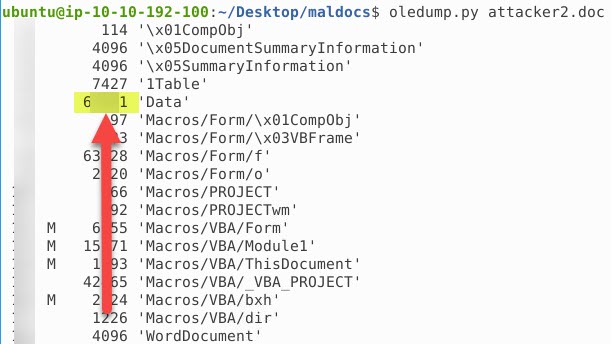
- Find the command located in the ‘fun’ field (make sure to reverse the string)
- c** /k *******.*** *:\***********\***.**s
We are going to use the tool oledump.py again and this time leverage the options -s to specify which stream we want to dump and -v to decompress any compressed VBAs. Run oledump.py -s 16 -v attacker2.doc

- Provide the first domain found in the maldoc
- p***********.***/***********/**.***l
We can use the strings command again and since we are asked to look for a domain, we can narrow our search through grep. Run strings attacker2.doc | grep https

- Provide the second domain found in the maldoc
- p***********.***/**********/**.***l

- Provide the name of the first malicious DLL it retrieves from the C2 server
- w***.**l
We can use the same command as above and just change the grep from https to dll.
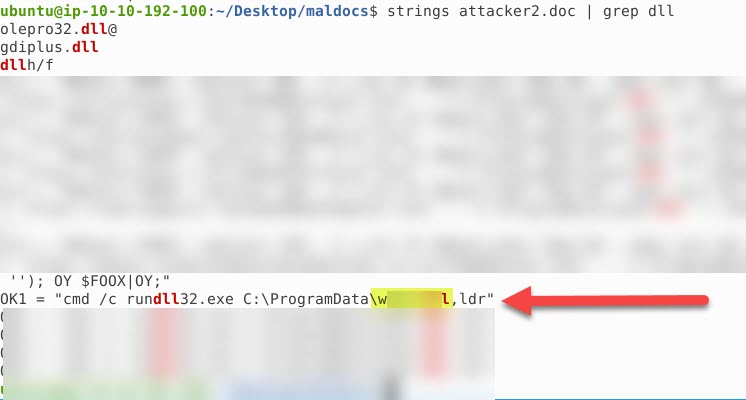
- How many DLLs does the maldoc retrieve form the domains?
- *
You can see the total number of DLLs from the image above.
- Provide the path of where the malicious DLLs are getting dropped onto
- C:\**********a
This information can be seen after running the oledump.py -s 16 -v attacker2.doc

- What program is it using to run DLLs?
- r*******.**e

- How many seconds does the function in the maldoc sleep for to fully execute the malicious DLLS?
- 1*
We can see that the WScript.Sleep is set to 15000. The 15000 is in milliseconds, so when you convert it to seconds, then you get your answer:

- Under what stream did the main malicious script use to retrieve DLLs from the C2 domains? Provide the name of the stream
- M*****/****/*
Here, I had to dump the streams individually to see which stream is the main malicious script residing.
Attacker 3:
- Provide the executable name being downloaded
- *.**e
Dump the streams individually using oledump.py. Run oledump.py -s A3 -v attacker3.doc

- What program is used to run the executable?
- C******l
We can use the image above this question to retrieve the program:
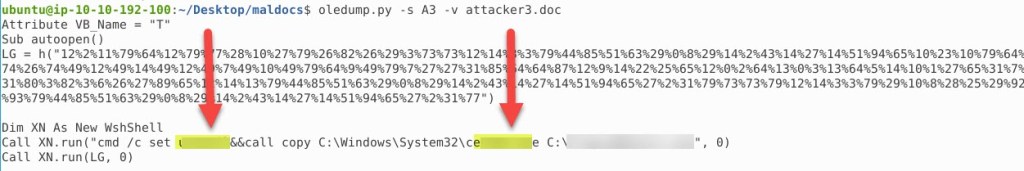
- Provide the malicious URI in the maldoc that was used to download the binary
- 8*****.***/****/*****.***?*=*****.**b
For this, I uploaded the maldoc to hybrid-analysis.com to find the answer.

- What folder does the binary gets dropped in?
- P*********a
I just guessed this one again
- Which stream executes the binary that was downloaded?
- A*
You can look back at 3 images above and see which stream we dumped that executes the binary.
Attacker 4:
- Provide the first decoded string found in this maldoc
- M*****.******P
- First, we dump stream 7 of the maldoc since that is the only stream with a macro. Run oledump.py -s 7 -v attacker.doc

2. And when you scroll down, you will see a lot of encoded strings, and we are asked to find out the first decoded string. Below is the first encoded string we can find. We have some clues to convert the encoded string from Hex and decrypt it using XORI. I have highlighted the clues below. The first set of strings is what we have to convert from Hex, and if you Google about XORI, you will learn that the second set of the encoded strings is the key to use to decrypt using XOR.

3. Load the first string to CyberChef, use the From Hex option, then use the XOR and enter the key as Hex:

- Provide the name of the binary being dropped
- D**********.**e
I used hybrid-analysis.com on this one again. If you look at the results of the analysis and scroll all the way down to the Extracted Files section, we will see the binary file.

- Provide the folder where the binary is being dropped to
- T***
I guessed again as there are not many folders with 4 characters as its name where files are normally dropped too.
- Provide the name of the second binary
- b**.**e
Again this was from hybrid-analysis.com

- Provide the full URI from the second binary was downloaded
- g*-****.**/**/***.**e
Look at the image before this question and you will see the domain that was used and all that needs to be done is to put the two together.
Attacker 5:
- What is the caption you found in the maldoc?
- C**********************e
Use the strings tool again here. Run strings attacker5.doc then scroll to look for the caption:

- What is the XOR decimal value found in the decoded base64 script?
- **
- Dump the streams one by one and look for strings. Run oledump.py -s 7 -S attacker5.doc

2. The above looks like a base64 encoded code. We have to decode it using CyberChef. Then to clean up the output, we can use Remove whitespace and Remove null bytes:

3. The output above looks like another base64 encoded code. We will do the same thing, but this time we have to add the gunzip tool because the code looks like it was also compressed:
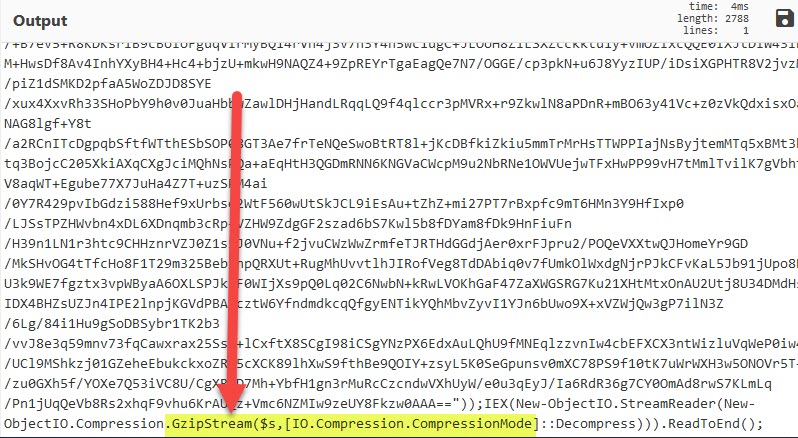
This is how it looks like after completely decoding the code properly:

- Provide the C2 IP address of the Cobalt Strike server
- 1**.***.**.*9
- From the image above we see that there is another base64 encoded message and that we have to use XOR with a value to decrypt the message.

2. Now, let’s look at the output and you can actually see some human-readable messages, like the IP address:

- Provide the full user-agent found.
- M******/*.* (**********; **** *.*; ******* ** *.*; *******/*.*; .N

- Provide the path value for the Cobalt Strike Shellcode
- /***R
I leveraged virustotal.com to retrieve this information:
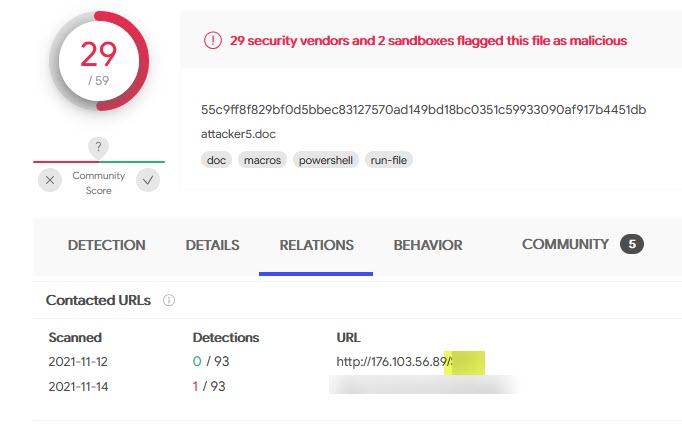
- Provide the port number of the Cobalt Strike C2 Server
- 8***

- Provide the first two APIs found
- L***********, ************A
This was the question where I struggled the most, as I can’t seem to find using online sandboxing malware analysis tools or even with the tools that I know. So, I went and looked at the Discord channel. Someone suggested the tool scdbg. It took me some time to read about this shell code debugger analysis application. To make the story short, run scdbg -f filename -s -1
- I downloaded scdbg on my Windows machine using this link.
- Then downloaded the output from CyberChef:

3. Now, run the scdbg tool to analyze the download.dat that we download in the previous step. Run .\scdbg.exe -f ‘download.dat’ -s -1

If you look at the image above, it would have made things easier for me to look for the answers instead of looking through hybrid-analysis and virustotal. The image above also included the full user-agent, the IP address of the Cobalt Strike C2 server, and also the port number used. Well, I have learned so much from this room. I was able to utilize tools that I haven’t used before. This room has definitely improved my blue teaming skills.
I hope you enjoyed my write-up. It was long, but it was all worth it and hopefully, you will find this helpful. Please don’t forget to subscribe to my blog.

Hi, I came across your blog on CEH Practical certification in “medium”. I have few quries regarding that exam. It would be very kind of you to help. I was not able to find your mail id, that’s I approaching in this way. nkrohitkumar2002@gmail.com – is my mailid. Kindly mail me, if you want to talk further
LikeLike
Wouldn’t let me comment on mobile. *shrug* Anyway, well done as always. I am very impressed with your skills and these write-ups are amazing.
LikeLike