I am writing this comparison between the FOR500 (GCFE) and 13Cubed Investigating Windows Endpoints based on my experience studying both the study materials and taking their respective certification exams.
I sat and passed the GCFE on 8/6/2024: 
I got certified in Investigating Windows Endpoints on 8/16/2024: 
First, I want to give a shout-out to Health Catalyst for believing in investing in their employees’ education/training. I wouldn’t pay $9,000+ out of my own pocket for a SANS class and certification. A $695 course and certification is way more affordable, and a military discount brings the price down to almost $600.
Let’s get to the bread and butter of this blog post.
- How are the course contents compared to each other?
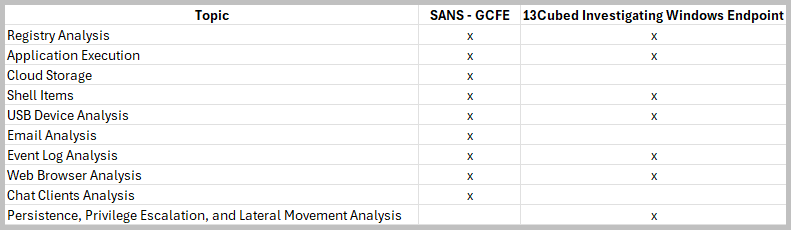
- How long is the training?
- I am comparing the SANS on-demand here because 13Cubed only offers on-demand training.
- FOR500 – ~30 hours
- 13Cubed – ~ 11 hours
- How much access time do I get?
- FOR500 – 4 months
- 13Cubed – 365 days
- What is the certification exam like?
- FOR500 – You take the GIAC Certified Forensic Examiner (GCFE), a proctored exam with 82 questions. 75 multiple-choice questions and seven cyberlive (practical) questions. You have 3 hours to complete the test and a minimum passing score of 70%.

- 13Cubed – You take the Knowledge Assessment at the end of the course. Non-proctored with 80 questions. 60 multiple-choice questions worth 1 point each, and 20 practical questions worth 2 points each. There is no time limit to taking the test, and a minimum of 70 points to pass the test.

- FOR500 – You take the GIAC Certified Forensic Examiner (GCFE), a proctored exam with 82 questions. 75 multiple-choice questions and seven cyberlive (practical) questions. You have 3 hours to complete the test and a minimum passing score of 70%.
- How hard was the exam?
- FOR500 – This is easier for me. Don’t get me wrong; the time constraint makes this exam hard. If you have a good index, it will be easy to find the answers to the multiple-choice questions because they are almost word-for-word out of the books. The cyber live part is even easier than the multiple-choice questions. This exam part will be a breeze if you do the cyber live labs at least twice. This is my third GIAC certification, and I’ve always found the cyber live questions easier than the multiple-choice part. For the cyber live, each question felt like a standalone to check your familiarity/knowledge of a certain tool.
- 13Cubed – This is a challenging exam. Both the multiple-choice part and the practical are tough to crack. In most of the multiple-choice questions, you really have to stop and think about the situation. For example (this is just an example), in the lesson, he talks about Event ID 7045 to investigate whether a new service was installed, but in the exam, you will have to use 4697. I liked it because I was forced to look for other avenues and not rely on what exactly came out of his mouth during the training. And don’t even get me started about the practical part. I would do 13Cubed’s practical 100% over the FOR500. The practical part questions are connected to each other. You are given a disk image of a compromised machine and will perform tasks like a black box approach. You don’t know anything about the image. You will have to perform an analysis from System/User profiling all the way to what activities the threat actor did, like, was there lateral movement? Privilege escalation? Post-exploitation? And so on. After doing the practical part, I felt like I came out as a Zimmerman tools expert (not really an expert; that was overexaggeration. Haha). Even better, you use your own machine, not a VM that sometimes can be riddled with issues. I’ve seen a lot of Reddit posts where people complained about VM issues during cyber live.
- Is there a possibility of cheating during the exam?
- FOR500 – Cheating is almost impossible because this is a proctored exam.
- 13Cubed – There is a big opportunity for cheating here. I am unsure if the questions change, but since this is not proctored and you can access the questions anytime, someone who wants to “get” the certificate just to say they are certified can have someone else take the exam for them. I hope everyone who takes this course and exam will do everything to keep the integrity of the certification exam because the exam is an excellent testament to the certified individual that they can perform Windows forensics.
- What are the forensic tools you’ve learned from the course?
- FOR500 – A combination of open-source tools and commercial tools like the USB Detective, Browser History Examiner, AXIOM, and Metaspike’s Forensic Email Intelligence. It was nice for SANS to include commercial tools because if you don’t work for large companies, it is almost impossible to get hands-on experience running them. The suite of Magnet Axiom tools is something that I would want in my tool bag when doing forensics.
- 13Cubed—All open-source tools. It is very heavy on Eric Zimmerman’s tools. Plaso and creating a super timeline, even when it took a long time to generate one, is also must.
- What was taking the course like?
- FOR500—There is too much content, especially for beginners. I felt like I was drinking straight from a fire hose. The videos are well-made, but it was death-by-powerpoint. If I remember correctly, even the command demonstrations were on PowerPoint.
- 13Cubed – After completing the course materials, I hoped there would be more. The videos are not long. I think the longest video is in the high 20s minutes. No PowerPoint slides except for some PDF cheat sheets, and all demonstrations were done with the hands-on keyboard. Richard shows you step-by-step where the .hve file comes from before running it in a command. It makes it easier to follow along. Like for example, watching him do a reboot three times to show you how ShimCache works (And it was worth it).
- Course materials:
- FOR500—You will be provided with physical books. I like that they give out books because it is easier to skim through pages if I am looking for particular information that I want to review, and I don’t have to go through the videos again. Also, highlighting the pages makes it easier to remember the important items.
- 13Cubed – No physical books, only videos and a handful of cheat sheets. You have to take notes so you don’t have to go over the videos again to get the answers to the questions.
- Which one do you recommend to take?
- Both courses are amazing. They both have their strong suits. But here’s my honest take. If you have not taken any courses and are still torn about which one to take, I recommend doing the 13Cubed Investigating Windows Endpoints first. My reasons for picking 13Cubed first are:
- More bang for your buck. $695 compared to $9,000+?
- The amount of material is less daunting. The topics in the course are enough to equip someone to start doing online forensic challenges and real-world forensics.
- Richard taught things that I wished FOR500 included—even small things, such as the “Collapse All Loaded Hives” in Registry Explorer and the use of the “Format” option when looking at the details in Timeline Explorer. These are small things, but they were a big help, especially during practical analysis. The use of Plaso/Log2Timeline was not discussed in FOR500.
- The military discount is a big help for me.
- My favorite part of the course is when Richard tells you about an artifact and repeatedly repeats which artifacts are unacceptable for evidence of execution. He says it so often that by the end of the course, as soon as you see the artifact, you know it cannot be used as evidence. Another one that was drilled into my head is the MACB. Go through the course, and you will understand what I mean (hahaha).
- Richard’s teaching style and explanations are more beginner-friendly. I appreciate it when he provides historical information on artifacts that were not meant for forensics in the beginning.
- I thought Event Log Analysis, Prefetch, Shimcache, AmCache, MUICache, UserAssist, SRUM, LNK Files, Jump Lists, and $I30 were better explained and easier for me to understand.
- I am not saying not to take the FOR500. Take it if possible, especially if your employer pays for the course. I learned a lot from FOR500. Topics like Cloud Storage, Email Analysis, and Deep Dive of Browser Forensics are treasures in FOR500. I still look at my index and the course books when I do online forensic challenges. And GCFE is a big name in the certification industry. FOR500 will feel less overwhelming after taking the 13Cubed Investigating Windows Endpoints. You can have the best of both worlds if you have the time and resources to do it.
In conclusion, you will get the same core skills to start doing Windows Endpoint Forensics in 13Cubed as in FOR500 without breaking the bank. There are even subjects where I think 13Cubed did better in teaching than FOR500. But again, it is all up to you to decide. If you want an affordable option that offers almost the same content, with more access time, and better knowledge assessment, but not an industry-recognized certification, then go with 13Cubed. No search results came up when I searched “13Cubed” on job sites like Indeed. This means that there are no job descriptions/requirements/certifications out there that include 13Cubed as a recognized certification. 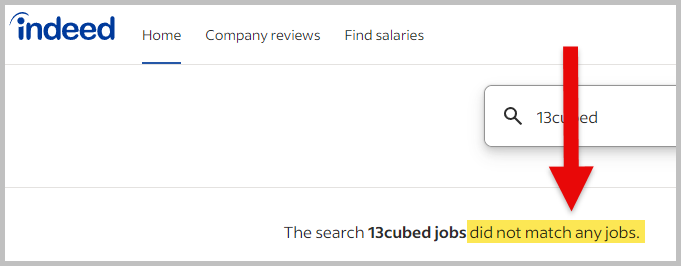
And, it is the exact opposite when searching for “GCFE”: 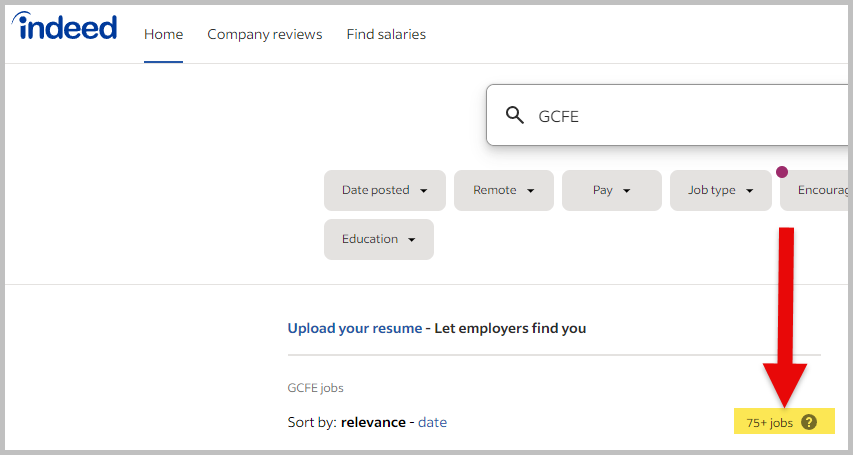
I am a big advocate of “learning never stops.” I hope to do 13Cubed’s Investigating Windows Memory and Investigating Linux Devices in the near future, but I still need both the FOR508 (GCFA) and FOR572 (GNFA) to complete my SANS Incident Response Graduate Certificate.
Within 5 minutes of submitting my exam, I got this email: 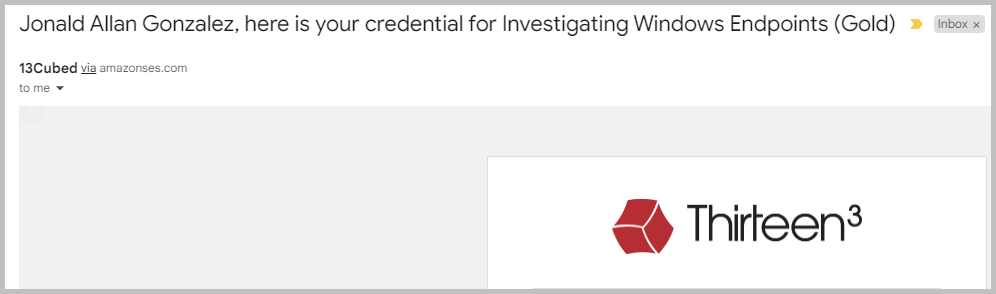
I hope you find the information I shared to be helpful. If you have any questions, please don’t hesitate to reach out.
Again, the things I shared here are based on what I remember from both courses and exams. Everything I wrote was about my honest feelings and opinions.
Awesome! Thank you for comparing the two. Dang that SANS is a lot of $$$
LikeLike
This is a nice write up on the 2 courses. I have taken the Richard Davis 13Cubed course and really enjoyed it and found it challenging. I have been doing DFIR for several years but learned a lot in the course. I have the opportunity to take FOR500 now and hope to have a good experience.
Thanks for the comparison!
LikeLike
Nice comparison mate. I have 4 GIAC certs under my belt, done in a 6 month period( GFACT,GSEC,GSOC,GCIH). Looking to get into forensics and have my eye on FOR500, but I don’t think my employer is that keen on my doing another SANs course so might go solo on this one. Any chance I can have a copy at your index?
Anyways good write up.
LikeLike