This Blue Team challenge was released on 7/23/2022 from CyberDefenders. You can access the room at https://cyberdefenders.org/blueteam-ctf-challenges/95.
This is one of the easiest challenges I’ve ever encountered from CyberDefenders.org. This is a perfect challenge for beginners who just want to get their feet wet in doing hacking/IR challenges. The skills/tools to be tested and needed to complete this challenge are looking at the code used by the phishing actor through any text editor/viewer and also a little bit of research on how Telegram works.
I hope you will find my write-up helpful.
First, download the challenge file and unzip it:

- Which wallet was used for asking the seed phrase?
- m*******
- Browse to c75-GrabThePhisher > pankewk > metamask
- Open the file metamask.php with your choice of text editor/viewer

- What is the file name that has the code for the phishing kit?
- m*******.***

- In which language was the kit written?
- p**

- What service does the kit use to retrieve the victim’s machine information?
- s**** ***

- How many seed phrases were already collected?
- *
- Browse to c75-GrabThePhisher > pankewk > log
- Open log.txt

- Write down the seed phrase of the most recent phishing incident?
- f***** **** ******* ****** ******* ******* ******** ******* ***** **** ****** ******

- Which medium had been used for credential dumping?
- t*******
- Look inside the file metamask.php again

- What is the token for the channel?
- 5*********:***********************************

- What is the chat ID of the phisher’s channel?
- 5*********

- What is the alias of the phish kit developer?
- j***********

- What is the full name of the phish actor?
- M***** ********
- To find the full name of the phish actor, we have to use the information that we have on-hand like the Telegram userID, token, and url found inside the file metamask.php
- Read about the Telegram bot API from the page, https://core.telegram.org/bots/api#getchatmember
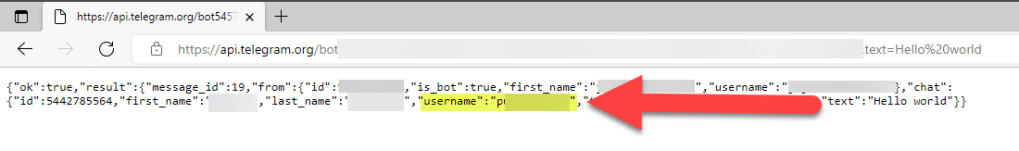
- We will have to utilize the sendMessage method in Telegram, passing the chatID and sending a random message through text.
- Enter the following to the URL bar: https://api.telegram.org/botenter_token_here/sendMessage?chat_ID= enter_userID_here&text=Hello_World


- What is the username of the phish actor?
- p**********
Thank you for checking my write-up. Please subscribe if you haven’t.
Nicely done. I like your write-ups. Easy to follow.
LikeLiked by 1 person
Thanks bro. Always good to know someone actually looks at my entries. Hahaha
LikeLike