Have you ever been in a situation where your organization stopped using cloud service and then realized that a valid certificate is still tied to the old IP address that you were assigned? That is the exact situation we were in, a scammy-looking gaming site was using the same IP address that our organization was assigned to before and was also using our valid certificate. 
It would have been easy to revoke the certificate but we have no idea which account was used to issue the certificate, and we didn’t want to wait 90 days for the certificate to expire. We also didn’t want the IP address to be attributed to our organization, optics will not be good. When we look at Letsencrypt’s documentation on certificate revocation: https://letsencrypt.org/docs/revoking/, they offer three ways to do it. (1) Revoke the certificate from the account that issued the certificate – which we don’t have, (2) Use the certificate private key – which we don’t have again, and (3) Use a different authorized account – our ONLY option left.
In this tutorial, I was using Kali.
Steps:
- Install Certbot by running: sudo apt-get install certbot

- Do a DNS Challenge to prove your ownership of the domain (NOTE: Use the entirety of the certificate’s Common Name when doing a DNS challenge. For some reason just doing the domain didn’t work for me). Type: sudo certbot -d your_domain.com –manual –preferred-challenges dns certonly

- You will be presented with a Name and a Value that you will need to create a TXT record into your domain registrar provider like GoDaddy.

- Here’s what it looks like in your domain registrar provider:

- Verify that the TXT record has been successfully deployed. Go to https://toolbox.googleapps.com/apps/dig and enter the name from Step 3.

- Once you have verified that the TXT record has been deployed, go back to the Certbot session you have and press Enter.

- Retrieve the Fingerprint of the certificate that you want to revoke and copy the value:

- Open a browser and visit https://crt.sh, and search for the certificate using the fingerprint you copied above, then download the certificate:

- It will download the file using a .crt extension. We need to change it into a .pem extension to continue with the revocation. You can just simply rename the file:

- Now, to revoke the certificate, run the command: sudo certbot revoke –cert-path your_cert_you_renamed.pem
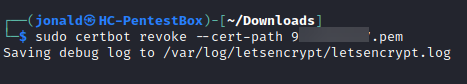
- Refresh the https://crt.sh session you have to check the revocation status:

- Don’t forget to remove/delete the TXT record.
We are all done! Congratulations on successfully revoking your certificate. I created this because I couldn’t find any HOW-TO with a detailed step-by-step online. I hope one of you will find this helpful.
If you haven’t, please subscribe to my blog!
Yes, yes I have seen this in our environment. Thank you for figuring this out and for fixing the issue!
LikeLiked by 1 person