This room was on 8/4/2023 and is rated easy in difficulty. Shout-out to the room creator, @1337rce. You can access the room at https://tryhackme.com/room/traverse.
Scenario: Bob is a security engineer at a firm and works closely with the software/DevOps team to develop a tourism web application. Once the website was moved from QA to Production, the team noticed that the website was getting hacked daily and wanted to know the exact reason. Bob consulted the blue team as well but has yet to be successful. Therefore, he finally enrolled in the Software Security pathway to learn if he was doing something wrong.
| Party | IP Address |
| My Device | 10.10.105.26 |
| Victim Host | 10.10.87.37 |
- What type of encoding was used by the attackers to obfuscate the JavaScript file?
- H**
- While viewing the “hacked” page, right-click and choose View Page Source.

- Looking at the HTML code, one comment stands out: THIS IS CUSTOM JS FILE. Check the script by clicking on the file custom.min.js

- A quick look at the characters used in the obfuscation, you should be able to guess what it is.
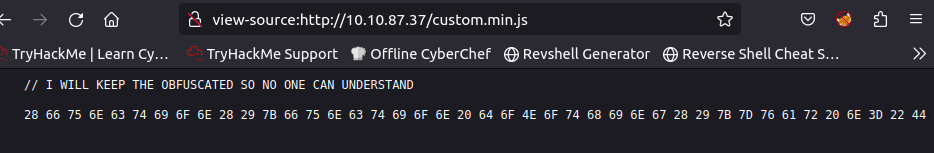
- What is the flag value after deobfuscating the file?
- D******** L****** I* T** O*** W**
- Copy the obfuscated string.
- Open CyberChef, and paste the copied string into the Input field.
- Drag the From Hex under the Operations column into the Recipe column.
- Under the Output field you will find the flag.

- Logging is an important aspect. What is the name of the file containing email dumps?
- e****_****.***
- Look at the Page Source again, and you will notice that there are directories that were listed that would at least give us an idea of what is inside the directories.

- The question stated about the importance of logging, so, let’s go to the /logs directory.
- Enter 10.10.87.37/logs in the URL bar of a browser.

- The logs folder contains email logs and has a message for the software team lead. What is the name of the directory that Bob has created?
- P*******
- Click the file you found inside the /logs directory in question 3, and you will be presented with an email message.
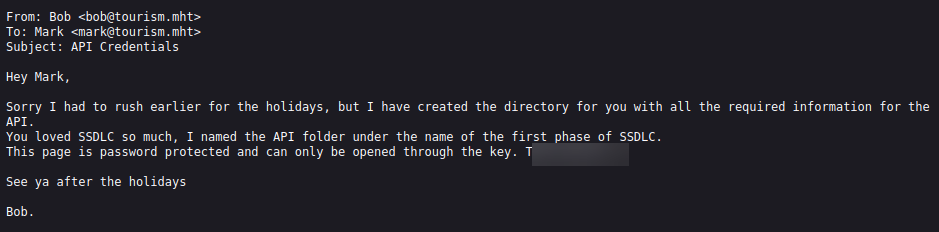
- Google search the Phases of Secure Software Development Life Cycle
- What is the key file for opening the directory that Bob created for Mark?
- THM{*********}
- Reference the email message in question 5 to retrieve the key file.
- What is the email address for ID 5 using the leaked API endpoint?
- j***@********.***
- Visit the site and add the directory that you found in question 4.

- You will see the API call from the above image that we can use to get the email address for the customer with ID number 5.
- Open a terminal and type GET http://10.10.87.37/api/?customer_id=5 | jq
- I added the jq to parse the json file into a more readable format

- What is the ID for the user with admin privileges?
- *
- Looking back to the image in question 6, we can see that the user John’s role is a user.
- You can repeat the GET command we used in question 6, and replace the id number until we find an account whose role is an admin

- What is the endpoint for logigging in as the admin? Mention the last endpoint instead of the URL.
- /*********
- We can reference the same image that we used in question number 7.

- The attacker uploaded a web shell and renamed a file used for managing the server. Can you find the name of the web shell that the attacker has uploaded?
- t**_*****.***
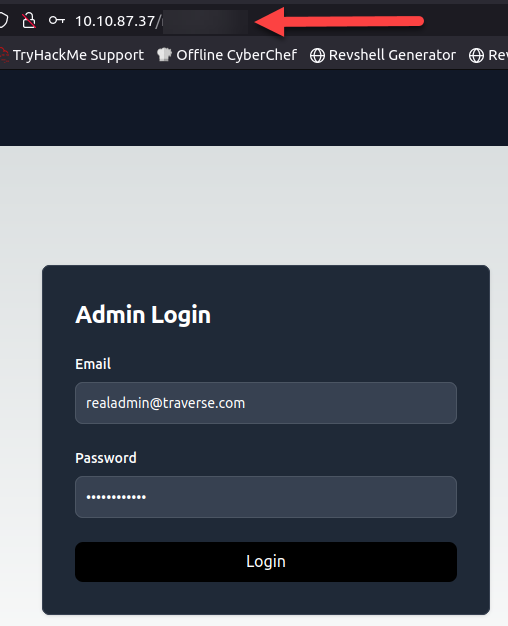
- Use the endpoint name that you found in question 8 to access the Admin Login Page.
- Use the email and password from question 8 to login.
- Once you are logged in, turn on FoxyProxy extension on your Firefox browser.

- Make sure that the Intercept is on on Burp Suite

- Press Execute

- Go back to Burp Suite, you will see that pressing the execute button is sending the command whoami to the web server.

- Let’s replace the command whoami to ls and see if the server will respond to a command that was not pre-programmed, then click the Forward button.

- Go back to the admin page and you will see a list of files and one of them is the web shell that was uploaded by the attacker.

- What is the name of the file renamed by the attacker for managing the web server?
- r******_****_*******.***

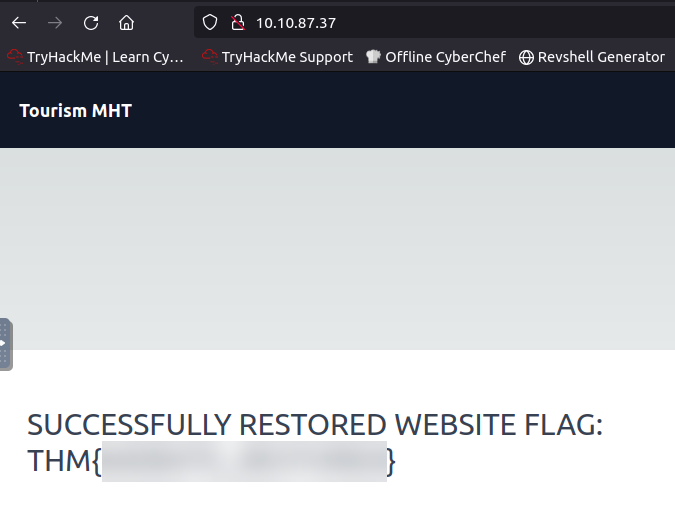
- Can you use the file manager to restore the original website by removing the FINALLY HACKED message? What is the flag value after restoring the main website?
- THM{*******_********}
- Browse to the Admin File Manager page. This is a combination of the directories you found on questions 8 and 10.

- The password to use to login was provided when you ran the command injection you performed on question 9.

- Look for the index.php file and click it.

- Hit the edit button, and change the variable message to something else other than the words FINALLY HACKED.

- I edited it to FIXED, then hit Save. And since the variable is not equal to FINALLY HACKED anymore, we should get our website back.

- Before

- After
I hope you will find my write-up helpful. Thank you again for visiting my page. Please subscribe if you haven’t done so. HAPPY HACKING!