
Scenario: An end-user device was infected by ransomware. A memory dump was captured from the compromised machine, and it is our task as digital forensics investigators to find the evidence of the attack.
The memory capture file that was provided to us is in .mans format which is a Mandiant Analysis File. This should give away the tool that we will be using to conduct the investigation, the Redline tool.
Difficulty: This challenge was rated as Medium in difficulty.
Analysis Prep:
- Open the .mans file in Redline.
- Review the questions from LetsDefend, so, we know what to look for.
Questions:
- Find the dropped dll, include the whole path including the dll file.
- C:\*****\*******\*******\*****\****\*****.dll
- Just by looking at the processes from the compromised machine, you will notice suspicious cmd.exe executions from unexpected locations such as the user’s temp folder.

- The image above gives us a hint where the dll file could have been dropped.
- Click FileSystem on the left column, type the unexpected location we found in the first bullet, apply a filter for anything that ends with .dll to get the answer to the firs question.

- Just by looking at the processes from the compromised machine, you will notice suspicious cmd.exe executions from unexpected locations such as the user’s temp folder.
- C:\*****\*******\*******\*****\****\*****.dll
- What is the MD5 hash for the dll?
- 0******************************c
- Double-click on the result of your search in question one. Make sure that you click on the details tab at the bottom of the Redline window, and you will find the hash value of the dll file.

- Double-click on the result of your search in question one. Make sure that you click on the details tab at the bottom of the Redline window, and you will find the hash value of the dll file.
- 0******************************c
- What is the name of the ransomware note that got dropped?
- 2****-*****e
- When we were looking at the Processes earlier, I noticed that Notepad.exe process was executed to open a file that was on the user’s Desktop.

- When we were looking at the Processes earlier, I noticed that Notepad.exe process was executed to open a file that was on the user’s Desktop.
- 2****-*****e
- What is the URL that the initial payload was downloaded from?
- http://***.***.**.***:****/*********/****s
- The question tells us exactly where to go to find the answer. The word “download” throws it away. So, go to the File Download History on the left column.
- Another hint is that there is only one entry with a download-type of manual, and the rest are auto.

- http://***.***.**.***:****/*********/****s
- The ransomware drops a copy of a legitimate application into the Temp folder. Please provide the file name including the extension.
- M******.**e
- This was another easy question because it tells us which folder to look into and since this is a Windows machine, we can assume that the legitimate application is an exe file.
- Search the Filesystem again for the user’s Temp folder and apply a filter of ends with .exe.
- There are not many as a result of the search, and you can pretty much guess which one is a legitimate application.
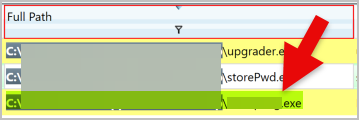
- M******.**e
- What is the name of the ransomware?
- S********i
- The answer to question number 3 is the key to answering this question.
- Go to FileSystem search for the user Desktop and apply a filter for ends with .txt.
- Click on the search result and make sure to choose the strings tab at the bottom.

- Copy the ransom note.

- Search it on Google and you will see search results that will tell you which ransomware the note is known from.

- S********i
Thank you for checking my blog post. Though this was rated by LetsDefend as a medium in difficulty, I thought it was really easy. Have fun and enjoy doing these fun challenges being offered to us by https://letsdefend.io.
Please subscribe to my blog if you haven’t done so.

Awesome! Appreciate the write up and guidance. Couldn’t do it without your help.
LikeLike